Cbeam 2002 Software Update
- CAESAR: Competition for Authenticated Encryption: Security, Applicability, and Robustness (2014), http://competitions.cr.yp.to/caesar.html
- Whiting, D., Housley, R., Ferguson, N.: AES Encryption and Authentication Using CTR Mode and CBC-MAC. IEEE 802.11-02/001r2 (2002)Google Scholar
- Rogaway, P., Bellare, M., Black, J., Krovetz, T.: OCB: a block-cipher mode of operation for efficient authenticated encryption. In: Reiter, M.K., Samarati, P. (eds.) ACM Conference on Computer and Communications Security, pp. 196–205. ACM (2001)Google Scholar
- Rogaway, P.: Efficient instantiations of tweakable blockciphers and refinements to modes OCB and PMAC. In: Lee, P.J. (ed.) ASIACRYPT 2004. LNCS, vol. 3329, pp. 16–31. Springer, Heidelberg (2004)CrossRefGoogle Scholar
- Krovetz, T., Rogaway, P.: The software performance of authenticated-encryption modes. In: Joux, A. (ed.) FSE 2011. LNCS, vol. 6733, pp. 306–327. Springer, Heidelberg (2011)CrossRefGoogle Scholar
- Bellare, M., Rogaway, P., Wagner, D.: The EAX mode of operation. In: Roy, B., Meier, W. (eds.) FSE 2004. LNCS, vol. 3017, pp. 389–407. Springer, Heidelberg (2004)CrossRefGoogle Scholar
- Bertoni, G., Daemen, J., Peeters, M., Van Assche, G.: Sponge functions. In: ECRYPT Hash Function Workshop (2007)Google Scholar
- Bertoni, G., Daemen, J., Peeters, M., Van Assche, G.: On the security of the keyed sponge construction. In: Symmetric Key Encryption Workshop (SKEW 2011) (2011)Google Scholar
- Bertoni, G., Daemen, J., Peeters, M., Van Assche, G.: Duplexing the sponge: Single-pass authenticated encryption and other applications. In: Miri, A., Vaudenay, S. (eds.) SAC 2011. LNCS, vol. 7118, pp. 320–337. Springer, Heidelberg (2012)CrossRefGoogle Scholar
- Aumasson, J., Jovanovic, P., Neves, S.: NORX v1 (2014), Submission to CAESAR competitionGoogle Scholar
- Dobraunig, C., Eichlseder, M., Mendel, F., Schläffer, M.: Ascon v1 (2014), Submission to CAESAR competitionGoogle Scholar
- Minaud, B.: Re: CBEAM Withdrawn as of today! (2014), CAESAR mailing listGoogle Scholar
- Saarinen, M.: CBEAM r1 (2014), Submission to CAESAR competitionGoogle Scholar
- Saarinen, M.: CBEAM: Efficient authenticated encryption from feebly one-way φ functions. In: Benaloh (ed.) [9], pp. 251–269Google Scholar
- Morawiecki, P., Gaj, K., Homsirikamol, E., Matusiewicz, K., Pieprzyk, J., Rogawski, M., Srebrny, M., Wójcik, M.: ICEPOLE v1 (2014), Submission to CAESAR competitionGoogle Scholar
- Bertoni, G., Daemen, J., Peeters, M., Van Assche, G., Van Keer, R.: Keyak v1 (2014), Submission to CAESAR competitionGoogle Scholar
- Andreeva, E., Bilgin, B., Bogdanov, A., Luykx, A., Mendel, F., Mennink, B., Mouha, N., Wang, Q., Yasuda, K.: PRIMATEs v1 (2014), Submission to CAESAR competitionGoogle Scholar
- Saarinen, M.: Beyond modes: Building a secure record protocol from a cryptographic sponge permutation. In: Benaloh (ed.) [9], pp. 270–285Google Scholar
- Saarinen, M.: STRIBOB r1 (2014), Submission to CAESAR competitionGoogle Scholar
- Saarinen, M.: Authenticated encryption from GOST R 34.11-2012 LPS permutation. In: CTCrypt 2014 (2014)Google Scholar
- Alizadeh, J., Aref, M., Bagheri, N.: Artemia v1 (2014), Submission to CAESAR competitionGoogle Scholar
- Gligoroski, D., Mihajloska, H., Samardjiska, S., Jacobsen, H., El-Hadedy, M., Jensen, R.: π-Cipher v1 (2014), Submission to CAESAR competitionGoogle Scholar
- Bellare, M., Namprempre, C.: Authenticated encryption: Relations among notions and analysis of the generic composition paradigm. J. Cryptology 21(4), 469–491 (2008)CrossRefzbMATHMathSciNetGoogle Scholar
- Iwata, T., Ohashi, K., Minematsu, K.: Breaking and repairing GCM security proofs. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 31–49. Springer, Heidelberg (2012)CrossRefGoogle Scholar
- Bertoni, G., Daemen, J., Peeters, M., Van Assche, G.: Sponge-based pseudo-random number generators. In: Mangard, S., Standaert, F.-X. (eds.) CHES 2010. LNCS, vol. 6225, pp. 33–47. Springer, Heidelberg (2010)CrossRefGoogle Scholar
- Bellare, M., Rogaway, P.: The security of triple encryption and a framework for code-based game-playing proofs. In: Vaudenay, S. (ed.) EUROCRYPT 2006. LNCS, vol. 4004, pp. 409–426. Springer, Heidelberg (2006)CrossRefGoogle Scholar
- Andreeva, E., Bilgin, B., Bogdanov, A., Luykx, A., Mennink, B., Mouha, N., Yasuda, K.: APE: Authenticated permutation-based encryption for lightweight cryptography. In: Cid, C., Rechberger, C. (eds.) FSE. LNCS. Springer (2014)Google Scholar
- Jovanovic, P., Luykx, A., Mennink, B.: Beyond 2c/2 security in sponge-based authenticated encryption modes. Cryptology ePrint Archive, Report 2014/373 (2014), Full version of this paperGoogle Scholar
- Wu, H.: The Hash Function JH (2011) Submission to NIST’s SHA-3 competitionGoogle Scholar
- Bagheri, N.: Padding of Artemia (2014), CAESAR mailing listGoogle Scholar
- Benaloh, J. (ed.): CT-RSA 2014. LNCS, vol. 8366. Springer, Heidelberg (2014)zbMATHGoogle Scholar
Cbeam 2002 Software Download
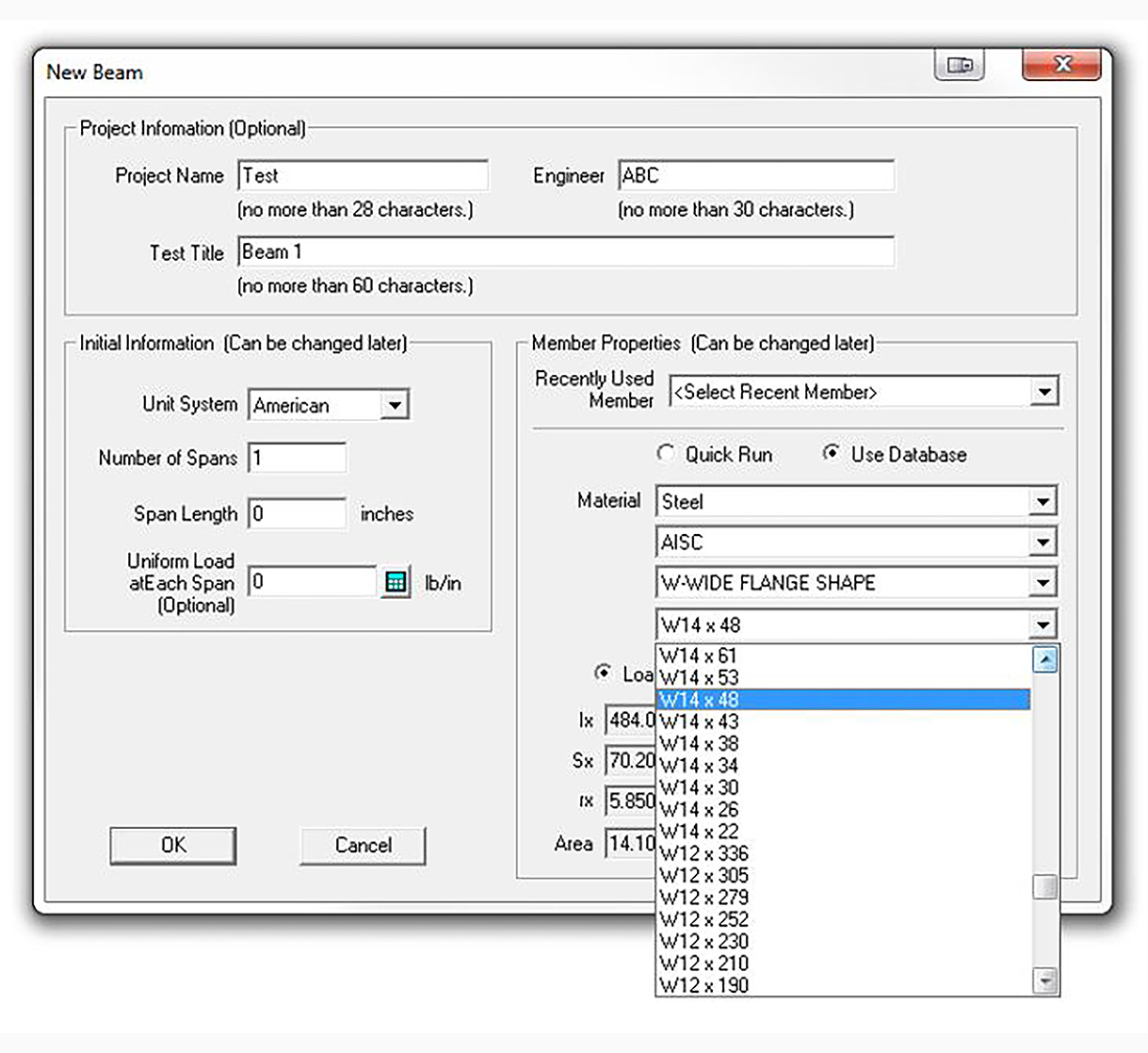
CBeam is a time saving and helpful tool to virtually any engineer, and it is an excellent compliment to any design or analysis software. With CBeam, a composite beam section can be created and edited graphically using any combination of rectangle, triangle or I-beam shapes. Cbeam is a continuous beam software package that allows the user to solve statically indeterminate beam structures. Multiple span elements of like or varying elasticity, along with uniform, distributed, and concentrated loads, and defined support and hinge conditions are available to the user. There were three problems I found during the build. The first is the video needs to be updated to include the Blackbox. The video shows a control board I couldn't even find on the website. There is a video for the Blackbox that does cover the build process and how to connect and install the software. Steel Beam Design Software - Free Download Steel. Steel Beam Design Software BEAM v.2.2.1.5 Analysis of beams with differential equation of the curly axis of beam, multiple supports, building M, Q, P, U diagram, appearing in beam from attached external loads. Knowledge / Learning Software Database Partners About / Services. Knowledge and Learning Resources for Structural Engineering.